3.3 KiB
image-template
Purpose
This repository is meant to be a template for building your own custom Universal Blue image. This template is the recommended way to make customizations to any image published by the Universal Blue Project:
This template includes a Containerfile and a Github workflow for building the container image. As soon as the workflow is enabled in your repository, it will build the container image and push it to the Github Container Registry.
Prerequisites
Working knowledge in the following topics:
- Containers
- rpm-ostree
- Fedora Silverblue (and other Fedora Atomic variants)
- Github Workflows
How to Use
Template
Select Use this Template and create a new repository from it. To enable the workflows, you may need to go the Actions tab of the new repository and click to enable workflows.
Containerfile
This file defines the operations used to customize the selected image. It contains examples of possible modifications, including how to:
- change the upstream from which the custom image is derived
- add additional RPM packages
- add binaries as a layer from other images
- modify system files (like /etc/systemd/system.conf)
Workflows
build.yml
This workflow creates your custom OCI image and publishes it to the Github Container Registry (GHCR). By default, the image name will match the Github repository name.
Container Signing
Container signing is important for end-user security and is enabled on all Universal Blue images. It is recommended you set this up, and by default the image builds will fail if you don't.
This provides users a method of verifying the image.
-
Install the cosign CLI tool
-
Run inside your repo folder:
cosign generate-key-pair- Do NOT put in a password when it asks you to, just press enter. The signing key will be used in GitHub Actions and will not work if it is encrypted.
Warning
Be careful to never accidentally commit
cosign.keyinto your git repo.
-
Add the private key to GitHub
-
This can also be done manually. Go to your repository settings, under Secrets and Variables -> Actions
 Add a new secret and name it
Add a new secret and name it SIGNING_SECRET, then paste the contents ofcosign.keyinto the secret and save it. Make sure it's the .key file and not the .pub file. Once done, it should look like this: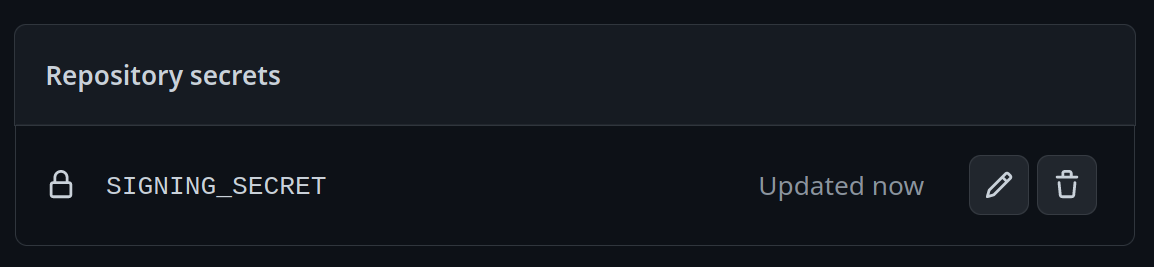
-
(CLI instructions) If you have the
github-cliinstalled, run:
gh secret set SIGNING_SECRET < cosign.key -
-
Commit the
cosign.pubfile into your git repository